Securing the copyright business need to be produced a precedence if we need to mitigate the illicit funding in the DPRK?�s weapons courses.
help it become,??cybersecurity steps may well turn into an afterthought, particularly when businesses deficiency the cash or personnel for such steps. The challenge isn?�t special to those new to business enterprise; on the other hand, even effectively-established providers may possibly let cybersecurity slide for the wayside or may absence the education to be familiar with the speedily evolving danger landscape.
copyright.US will not be liable for any reduction that you may possibly incur from price fluctuations any time you purchase, offer, or hold cryptocurrencies. Remember to refer to our Phrases of Use For more info.
Bitcoin employs the Unspent Transaction Output (UTXO) model, comparable to transactions with Actual physical dollars wherever Every single specific bill would wish being traced. On other hand, Ethereum employs an account model, akin to the checking account using a operating equilibrium, that's much more centralized than Bitcoin.
Even so, things get difficult when a person considers that in the United States and most nations around the world, copyright is still largely unregulated, plus the efficacy of its current regulation is usually debated.
These here threat actors had been then capable to steal AWS session tokens, the momentary keys that assist you to ask for non permanent qualifications to your employer?�s AWS account. By hijacking active tokens, the attackers were in a position to bypass MFA controls and obtain entry to Protected Wallet ?�s AWS account. By timing their attempts to coincide With all the developer?�s standard operate hrs, Additionally they remained undetected until finally the actual heist.
 Scott Baio Then & Now!
Scott Baio Then & Now!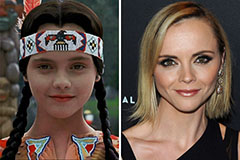 Christina Ricci Then & Now!
Christina Ricci Then & Now! Melissa Joan Hart Then & Now!
Melissa Joan Hart Then & Now!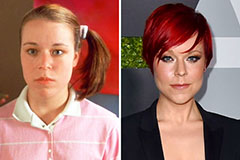 Tina Majorino Then & Now!
Tina Majorino Then & Now! Richard Thomas Then & Now!
Richard Thomas Then & Now!